Hackers can bypass Android fingerprint system with just a $15 equipment
GadgetByte Nepal
May 27, 2023

Fingerprint scanners have been an integral part of our smartphones, with almost every new model featuring one for biometrics. However, a recent study has revealed a security vulnerability in fingerprint scanners in many popular Android smartphones that can be exploited within 40 minutes with a new method called BrutePrint. In this article, I will provide a detailed understanding of the BrutePrint attack, its mechanism, the required conditions for success, and an analysis of the smartphones that are most vulnerable to this technology.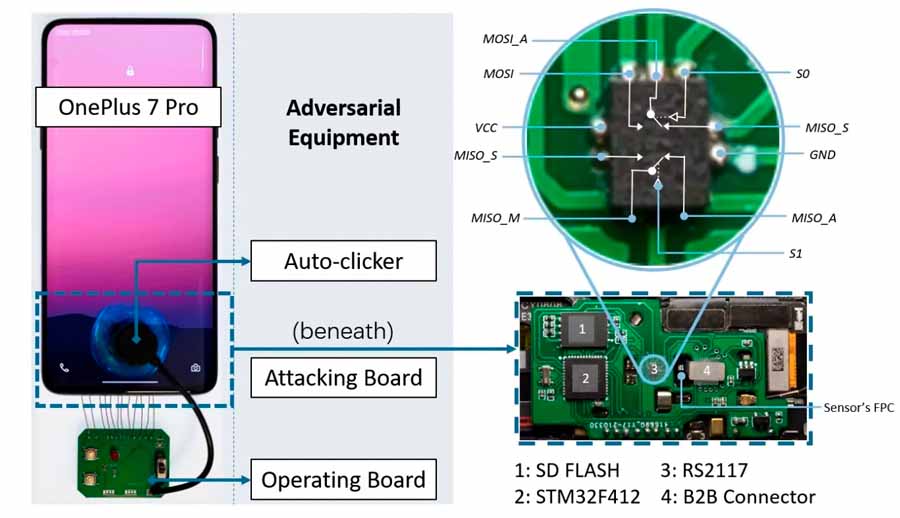
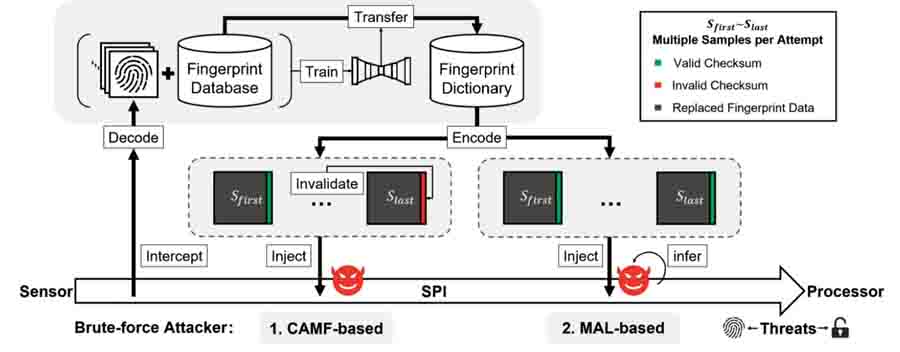 CAMF: It is a security measure that halts the authentication process when a fingerprint match fails. This allows potential attackers to attempt an unlimited number of fingerprints without triggering the security system.MAL: The MAL bug enables attackers to avoid the lockout mode, which typically activates after a certain number of failed authentication attempts and allows them to unlock the system infinitely.The method as a whole manipulates the reference fingerprint criteria to match it to that stored in the phone’s database.
CAMF: It is a security measure that halts the authentication process when a fingerprint match fails. This allows potential attackers to attempt an unlimited number of fingerprints without triggering the security system.MAL: The MAL bug enables attackers to avoid the lockout mode, which typically activates after a certain number of failed authentication attempts and allows them to unlock the system infinitely.The method as a whole manipulates the reference fingerprint criteria to match it to that stored in the phone’s database.
BrutePrint Overview:
Unlike password authentication, where an exact match is required between the entered password and the stored one, fingerprint authentication can be compromised by meeting a certain similarity threshold rather than an actual value. Researchers from Tencent Lab and Zhejiang University have introduced a new method called "BrutePrint" that allows unauthorized access to a smartphone with a fingerprint authentication security mechanism using a low-cost device priced at $15.Basically, BrutePrint means is the process of attempting to unlock a smartphone with a fingerprint lock without the actual owner's fingerprint. This action involves repeatedly comparing the data stored in the phone's internal components with a collection of breached fingerprints-trying to find a match.Required Equipment to carryout BrutePrint
The actual essentials involved in cracking the fingerprint security (applying BrutePrint):
- STM32F412 microcontroller
- RS2117, a dual-channel analog switch
- 8GB SD flash card
- A connector that connects a phone motherboard to the fingerprint sensor circuit board.
- You might also like:
Actual Mechanism of the BrutePrint Attacking
The BrutePrint attack involves attaching a circuit board with a pre-loaded fingerprint database to the targeted phone's processor, converting the database into a phone-compatible fingerprint dictionary, exceeding attempt limits, and exploiting zero-day vulnerabilities in the smartphone's fingerprint authentication framework, i.e., Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL).
Android and iPhone's Response to BrutePrint
The researchers conducted tests on eight Android phones to evaluate the effectiveness of the breakthrough. These phones included Xiaomi Mi 11 Ultra, Vivo X60 Pro, OnePlus 7 Pro, Oppo Reno Ace, Samsung Galaxy S10+, OnePlus 5T, Huawei Mate 30 Pro 5G, and Huawei P40. Among all the tested devices, the Xiaomi Mi 11 took the longest time to unlock (2.78 ~ 13.98 hours). In contrast, the Samsung Galaxy S10+ had the shortest unlocking time (0.73 ~2.9 hours).iPhones are supposedly immune to attack. When researchers tried the BrutePrint technique on iPhone models like the iPhone SE and iPhone 7, which have the Touch ID feature, they were unable to unlock these phones because of the strong data encryption provided by iOS.Factors Affecting Unlock Process Time
The unlock process using the technique can take anywhere from 40 minutes to 14 hours. It depends on factors like database size, software optimizations, the phone's security framework, and other variables.Recommendations to Enhance Fingerprint Security
To reduce attacks, the researchers who developed the approach have suggested the following adjustments at the hardware and software levels:- Checking if the attempt limits can exceed in any case.
- Encrypting data flow between the fingerprint sensor and device processor.
- Creating consistency in the way fingerprints are collected, whether the fingerprint matches or not.
- Meanwhile, check out our review of Galaxy M14.

To say something about myself, I have been writing tech and gadgets from 2021. Although coming from a non technical studies background, I'm someone who is always fascinated by the latest gadget and tech innovations, circling around. Besides writing, you'll find me listening music and aligning the stars through astrology and sometimes even, tarot cards! 😉🧿
Comments
No comments yet. Add a comment to start a discussion



